Hossein Shafagh
Since end of 2018, I have joined Netflix as a Senior Security Engineer in California.
At Netflix, I co-lead the PKI strategy efforts, co-own the TLS certificate lifecycle management service, and partner with cross-functional teams to help with secure system design aspects.
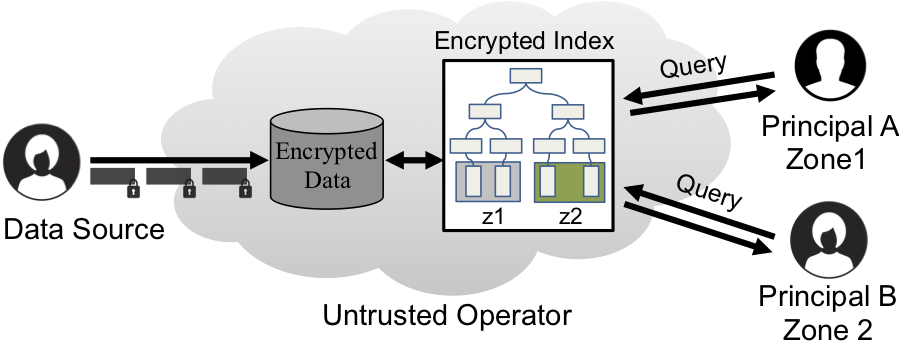
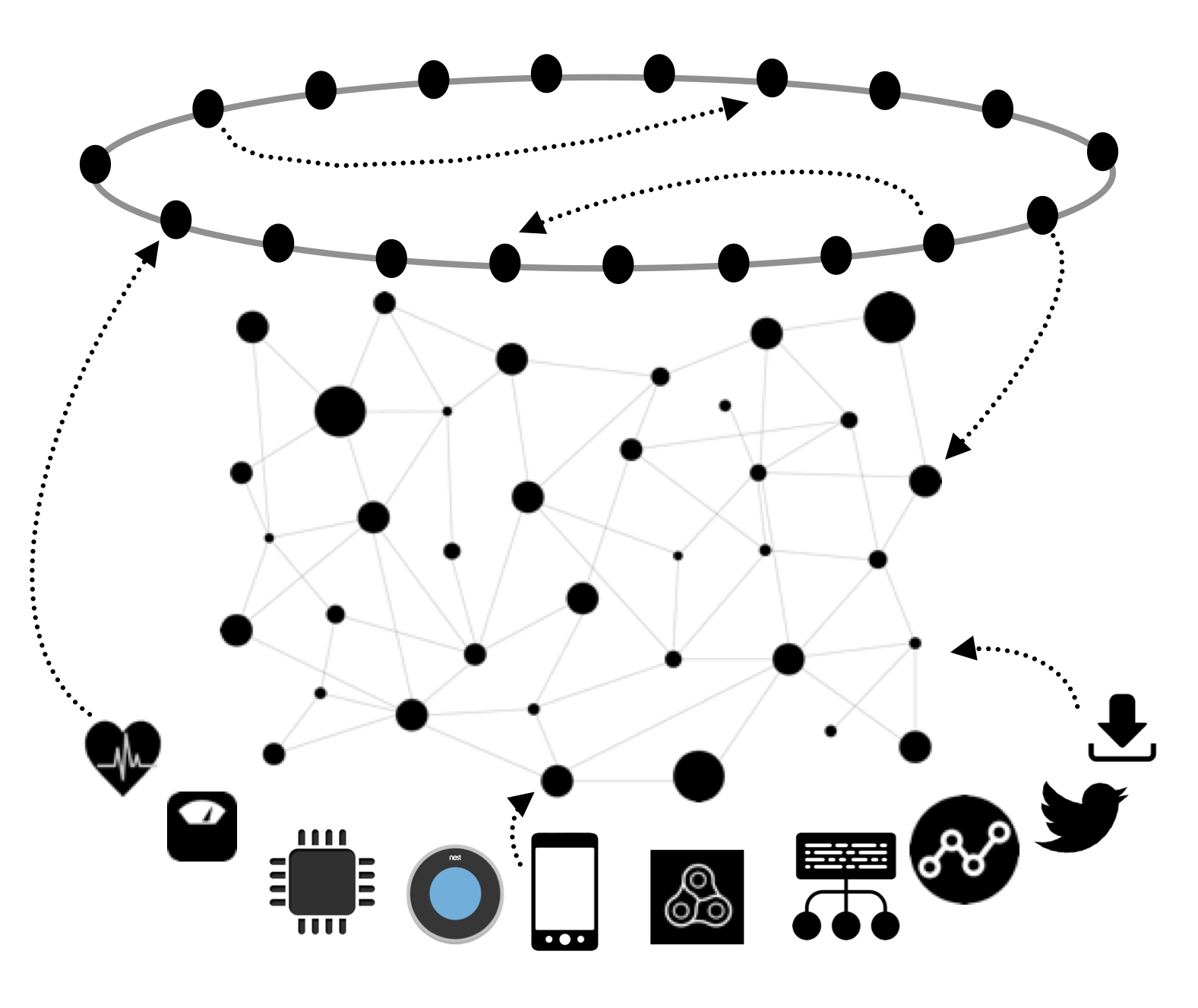
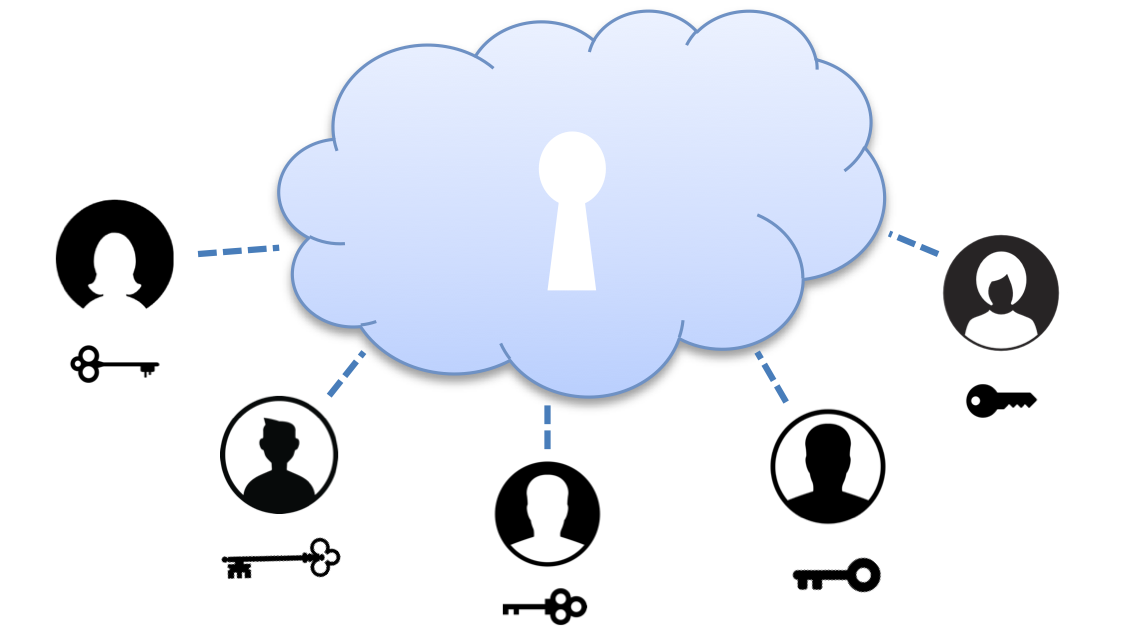
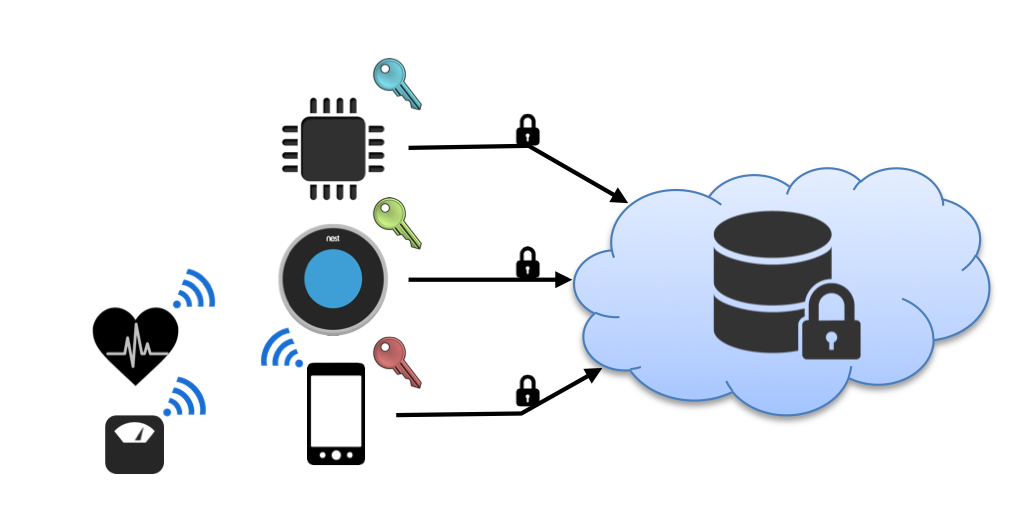
Prior to that I was a researcher at ETH Zurich, Switzerland, affiliated with the Distributed Systems Group. My research focus has been on enabling the vision of data ownership, where users retain control over their data, and service providers only see and process encrypted data. More specifically, I have designed and built encrypted data processing, and cryptographic-based authorization systems. In general, I follow research in the systems, networking, and security domain.
I obtained my Ph.D. from ETH Zurich in summer 2018. The title of my dissertation is "Retaining Data Ownership in the Internet of Things" (PDF) and my examination committee consisted of Prof. Philip Levis and my co-advisers Prof. Srdjan Capkun and Prof. Friedemann Mattern. Before that, I graduated with M.Sc. and B.Sc. degrees in Computer Science from RWTH Aachen University, Germany. I conducted my master's thesis at SICS (Swedish Institute of Computer Science) in the area of delegated public-key-based authentication for the Internet of Things. In summer 2015, I was a research intern at Stanford, with Philip Levis.
To learn more about our decentralized access authorization project Droplet check out: dropletchain.github.io
TimeCrypt is our encrypted time-series data analytics system: timecrypt.io
Talos is our encrypted data processing project: talos-crypto.github.io